The BGP Announcement Policy of Hong Kong Internet eXchange (HKIX) is as follows,
Improper Route Announcement
In case there is reported case about one HKIX participant announcing routes (no matter RTBH, or /24, etc.) that are not owned by that HKIX participant, HKIX will coordinate related parties to check with each other and may suspend the HKIX switch port if necessary. If you find improper route announcement on HKIX, please report the case to HKIX NOC at noc[@]hkix.net.
a. IP address filtering
- Applicable to general HKIX members.
- Filtering by IP addresses.
- Update^ via Filter Update Agent for each announcement.
b. IRR filtering
- Applicable to general HKIX members.
- Filtering by IP addresses.
- Update automatically from Internet Routing Registry database.
- Please register your AS-SET at IRR database.
^HKIX members should check the integrity of the IP address filters and submit only the IP addresses that require for update. HKIX may reject the applications if the IP addresses had already included in the filter.
The minimum IP block accepted by the HKIX route server is /24.
Route Prefix Advertisement Control by Standard BGP Community
HKIX route servers support route prefix advertisement control by standard BGP community. HKIX participants can use below standard BGP community to control BGP prefix advertisement, targets for 2-Byte AS number ($Peer-AS).
| Send prefix to all | 4635:4635 |
| Send prefix to $Peer-AS only | 4635:$Peer-AS |
| Do not send prefix to all | 0:4635 |
| Do not send prefix to $Peer-AS | 0:$Peer-AS |
- If there is none of BGP community, a prefix will be sent to all by default.
- Please use either Standard BGP Community or Large BGP Community for route prefix advertisement control, but do not use both at the same time.
- Please set only one type of above BGP community, while $Peer-AS can be multiple (for example 4635:65501 & 4635:65502 to announce a prefix only to AS65501 and AS65502, or 0:65501 & 0:65502 to announce a prefix to all but not to AS65501 and AS65502).
Route Prefix Advertisement Control by Large BGP Community
HKIX route servers support route prefix advertisement control by Large BGP community. HKIX participants can use below large BGP community to control BGP prefix advertisement, targets for 4-Byte and 2-Byte AS number ($Peer-AS).
| Send prefix to all | 4635:1:0 |
| Send prefix to $Peer-AS only | 4635:1:$Peer-AS |
| Do not send prefix to all | 4635:0:0 |
| Do not send prefix to $Peer-AS | 4635:0:$Peer-AS |
- If there is none of BGP community, a prefix will be sent to all by default.
- Please use either Standard BGP Community or Large BGP Community for route prefix advertisement control, but do not use both at the same time.
- Please set only one type of above BGP community, while $Peer-AS can be multiple (for example 4635:1:234567 & 4635:1:65501 to announce a prefix only to AS234567 and AS65501, or 4635:0:234567 & 4635:0:65501 to announce a prefix to all but not to AS234567 and AS65501).
HKIX supports RPKI on HKIX Route Servers starting from mid-Jun 2020 in order to enhance routing security
What is RPKI?
Resource Public Key Infrastructure (RPKI) is a public key infrastructure framework designed to secure the Internet’s routing infrastructure. RPKI, can be used to prevent route hijacking and misconfigurations.
How RPKI helps to prevent route hijacking?
RPKI certificate proves the association between specific IP address blocks and owner. HKIX can validate the legitimacy when HKIX participants send prefixes to HKIX Route Servers.
What is a ROA?
A Route Origin Authorization (ROA) associates a prefix with an origin AS number. ROA also provides the most specific prefix (maximum length) that the AS may announce.
How does HKIX Route Servers validate ROA?
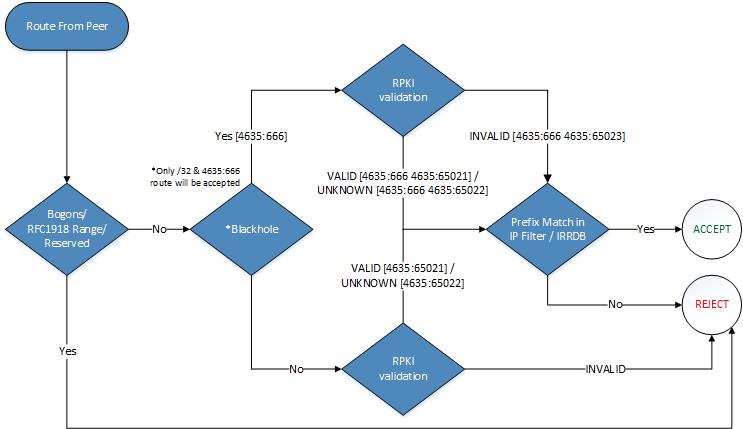
HKIX Route Servers validate ROA with RPKI validator that verifies RPKI objects as one of the three RPKI validity states and tag with standard BGP communities if appropriate:
- VALID: There is one ROA covers the BGP announcement, in terms of origin AS number, prefix and prefix length. (4635:65021)
- UNKNOWN: There is no ROA for the prefix, HKIX Route Servers will further check the prefix with either HKIX IP address filtering or IRR filtering. (4635:65022)
- INVALID: There is one ROA for the prefix, but either origin AS number or prefix length does not matched. HKIX Route Servers will reject these prefixes.
How can you create your ROA?
For the case of APNIC, you can log in your MyAPNIC account and follow the step-by-step guide.
For other Regional Internet Registry (RIR), please refer to:
AFRINIC https://afrinic.net/resource-certification
ARIN https://www.arin.net/resources/rpki
LACNIC https://www.lacnic.net/640/2/lacnic/general-information-resource-certification-system-rpki
HKIX RPKI Deployment FAQ:
- Do I need to implement RPKI in order to peer with HKIX Route Servers?
No, but in case you have RPKI ROAs configured, then your BGP announcement prefixes must be covered by the ROAs.
- What happen if I do not have ROA yet?
If you don’t have any ROA – You won’t be affected.
The RPKI validation status is UNKNOWN and the HKIX route servers will further check the prefix with either HKIX IP address filtering or IRR filtering.
- Will HKIX accept my blackholing (RTBH) prefix if it does not adapt the maximum prefix length (e.g. /32) in the ROA?
Yes, HKIX Route Servers will accept the /32 prefix for blackholing. It will be tagged with 4635:666 4635:65023 in the BGP announcement.
- How to verify my prefix after HKIX RPKI Deployment?
You can check your prefix and the validation status at HKIX Looking Glass.
|